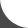Recommended Software
GreenBrowser 4.2.0712
GreenBrowser is a multiple windows browser based on IE with other powerful features. Such as: - Quick Key, Collector, Mouse Gesture, Mouse Drag, Ad Filter, Search Engine, Page Back Color, Toolbar Skin, Proxy, Tab Bar, Auto Scroll, Auto Save, Auto Fill Form, Start Mode, Auto Hide Bar, Mouse Drag...
DOWNLOADSoftware Catalog
 Android Android |
 Business & Productivity Tools Business & Productivity Tools |
 Desktop Desktop |
 Developer Tools Developer Tools |
 Drivers Drivers |
 Education Education |
 Games Games |
 Home & Personal Home & Personal |
 Internet & Networking Internet & Networking |
 Multimedia & Design Multimedia & Design |
 Operating Systems Operating Systems |
 Utilities Utilities |



Data Destroyer Feedback System
Data Destroyer Info
License: Shareware | Author: Hermetic Systems
When Windows 'deletes' a file it does not actually destroy the contents of the file but rather simply unlinks the file from the file directory system, leaving the contents of the file in the disk sectors. This data will remain there until the operating system uses those sectors when writing new data. Until the old data is overwritten (and this may take months or longer) it can be recovered by programs that read disk sectors directly, such as forensic software (so called because it is used to obtain evidence in criminal investigations and also in legal discovery).
In order to be sure that a deleted file really is deleted, gone for good, its contents never to be seen again, it is necessary to overwrite the data sectors of that file. Data Destroyer purges data in files, where 'purge' means to destroy, to eliminate completely by overwriting, so that the data cannot be recovered by any means. Data Destroyer allows you to destroy the contents of a file by overwriting it several times (or many times) with random bytes, and with bytes with alternating bit patterns, before the file is deleted (i.e., unlinked).
Data Destroyer can purge either: (a) a single file, (b) all files in a folder, (c) a specified subset of files in a folder, (d) all files in a folder and all files in all subfolders of that folder, (e) a specified subset of all files in a folder and in all subfolders of that folder, (f) all space on a disk and (g) all unused clusters on a disk.
This software checks for possible errors in user input, and is designed to minimize the chance of accidentally purging a file that you wish to keep.
Another feature of Data Destroyer is that you can get an accurate estimate of the time required to perform a purge operation. A lengthy purge operation may require several hours, or even days, and if you did not have an accurate estimate of the time needed before beginning the operation you might get worried, not knowing how long it still has to run.
Notice: * - required fields
Hermetic Systems Software
 Chinese Calendrics - A program to convert between dates in various Chinese calendars and dates in the Gregorian and Julian calendars, and to find lunar new year's day and leap months for any year in the Chinese Calendar.
Chinese Calendrics - A program to convert between dates in various Chinese calendars and dates in the Gregorian and Julian calendars, and to find lunar new year's day and leap months for any year in the Chinese Calendar. Cryptosystem ME6 - Windows software for encryption and decryption of single files or multiple files in a single operation for secure storage or secure transmission. It uses a 500-bit key for security, and has features designed to minimize the chances of user error.
Cryptosystem ME6 - Windows software for encryption and decryption of single files or multiple files in a single operation for secure storage or secure transmission. It uses a 500-bit key for security, and has features designed to minimize the chances of user error. Easy Date Converter - Adds a number of days to a date, calculates the number of days between two dates, and converts among dates in various solar calendars: Gregorian, Julian, ISO 8601 Week, Hermetic Leap Weak and day-in-year (yyyy-ddd).
Easy Date Converter - Adds a number of days to a date, calculates the number of days between two dates, and converts among dates in various solar calendars: Gregorian, Julian, ISO 8601 Week, Hermetic Leap Weak and day-in-year (yyyy-ddd). Easy Email Encryption - For encryption and decryption of email messages, optionally with attached files up to 100 KB in all. Keys are maintained in an encrypted list of keys for easy access and repeated use. Program is bilingual: English/German.
Easy Email Encryption - For encryption and decryption of email messages, optionally with attached files up to 100 KB in all. Keys are maintained in an encrypted list of keys for easy access and repeated use. Program is bilingual: English/German. Easy Graphics File Converter - Converts from GIF, JPG, PNG and BMP graphics files to JPG, PNG and BMP files. Allows single or multiple file conversion. Can convert to JPGs over a range of quality/compression values for optimization. Converted files displayed in your browser.
Easy Graphics File Converter - Converts from GIF, JPG, PNG and BMP graphics files to JPG, PNG and BMP files. Allows single or multiple file conversion. Can convert to JPGs over a range of quality/compression values for optimization. Converted files displayed in your browser. Easy HTML Construction Kit - This program includes an interactive TABLE generator which handles COLSPAN and ROWSPAN, and provides an easy way to create HTML code from lists and tables in textfiles, and to convert data in textfiles to finished HTML documents.
Easy HTML Construction Kit - This program includes an interactive TABLE generator which handles COLSPAN and ROWSPAN, and provides an easy way to create HTML code from lists and tables in textfiles, and to convert data in textfiles to finished HTML documents. Factorizer - A program to find prime numbers and pairs of primes, to decompose numbers into their prime constituents, to find all factors of any positive integer up to 2,147,483,645, and to plot Erdos-Kac and Palmen Color histograms.
Factorizer - A program to find prime numbers and pairs of primes, to decompose numbers into their prime constituents, to find all factors of any positive integer up to 2,147,483,645, and to plot Erdos-Kac and Palmen Color histograms. Five Cellular Automata - Software for exploring five cellular automata: q-state Life (a generalization of Conway's Life), the Belousov-Zhabotinsky Reaction, Togetherness, Viral Replication and Diffusion-Limited Aggregation.
Five Cellular Automata - Software for exploring five cellular automata: q-state Life (a generalization of Conway's Life), the Belousov-Zhabotinsky Reaction, Togetherness, Viral Replication and Diffusion-Limited Aggregation. Hermetic Stego - A steganography program which allows you to encrypt and hide a file of any size in BMP image files, with or without the use of a stego key, so that the presence of the hidden file is undetectable, even by software using statistical methods.
Hermetic Stego - A steganography program which allows you to encrypt and hide a file of any size in BMP image files, with or without the use of a stego key, so that the presence of the hidden file is undetectable, even by software using statistical methods. Hermetic Word Frequency Counter - This software scans a file, or text on the clipboard, and counts the number of occurrences of different words. The text can be in a language other than English. The words which are found and displayed can be ordered alphabetically or by frequency.
Hermetic Word Frequency Counter - This software scans a file, or text on the clipboard, and counts the number of occurrences of different words. The text can be in a language other than English. The words which are found and displayed can be ordered alphabetically or by frequency.

 Top Downloads
Top Downloads
- Evidence Begone Free Porn Scan
- Agnitum Outpost Firewall Pro
- PasswordsPro
- SpotMSN Password Recover
- Zip Password
- Win Spy Software Pro
- KeysRecover
- Internet Access Controller
- Internet SPY - PC Detective
- Webroot Spy Sweeper with AntiVirus

 New Downloads
New Downloads
- DiskPulse Server
- SpyAgent
- Passwords Base
- Network Password Manager
- Cryper
- PasswordsPro
- SpotMSN Password Recover
- IE Asterisk Password Uncover
- Master Voyager
- ProteMac NetMine

New Reviews
- jZip Review
- License4J Review
- USB Secure Review
- iTestBot Review
- AbsoluteTelnet Telnet / SSH Client Review
- conaito VoIP SDK ActiveX Review
- conaito PPT2SWF SDK Review
- FastPictureViewer Review
- Ashkon MP3 Tag Editor Review
- Video Mobile Converter Review
Actual Software
| Link To Us
| Links
| Contact
Must Have
| TOP 100
| Authors
| Reviews
| RSS
| Submit