Recommended Software
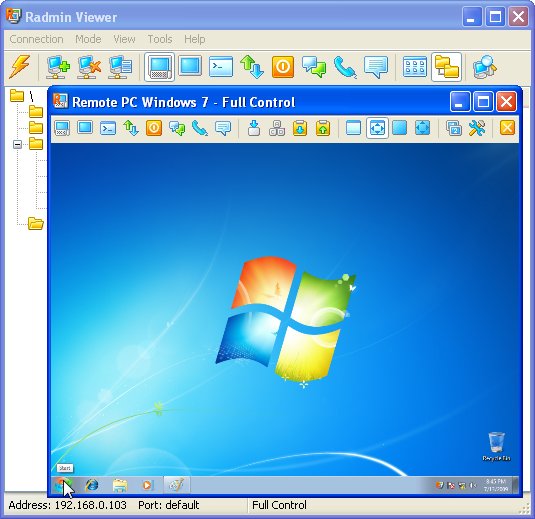
Radmin Remote Control 3.4
Radmin (Remote Administrator) is the famous remote administration software for remote computer control. It enables you to access a remote PC via a LAN or over the Internet in multiple modes: remote file access, remote assistance, full remote computer control, Telnet, text and voice chat. Strong...
DOWNLOADSoftware Catalog
 Android Android |
 Business & Productivity Tools Business & Productivity Tools |
 Desktop Desktop |
 Developer Tools Developer Tools |
 Drivers Drivers |
 Education Education |
 Games Games |
 Home & Personal Home & Personal |
 Internet & Networking Internet & Networking |
 Multimedia & Design Multimedia & Design |
 Operating Systems Operating Systems |
 Utilities Utilities |



Insider
Insider 3.02
Category:
Utilities / Security & Encryption
| Author: Janusware Ltd.
DOWNLOAD
GET FULL VER
Cost: $29.00 USD
License: Shareware
Size: 4.5 MB
Download Counter: 9
Requirements: Pentium Processor, 5MB Disk Space, VGA or Better Display
OS Support:
Language Support:
Related Software
Aes | Double file | Double Steganography | File Compression | File Compression Tool | File Compression Utility | File Encryption | File Hiding | Free file shred | Hide Files | Information Hiding | Program And Information Hiding | Shred | Shred file free | Unix shred file | Vb file shred
 Steganography - Steganography: an excellent method of embedding information on the contents of the file within another file! Make your secrets invisible in just 3 quick steps!
Steganography - Steganography: an excellent method of embedding information on the contents of the file within another file! Make your secrets invisible in just 3 quick steps! Max File Encryption - Max File Encryption is a powerful yet easy-to-use encryption/steganography software. With Max File Encryption, you can encrypt files, hide files and create self-decrypting packages. The program uses the strong Blowfish algorithm, ensuring data safety
Max File Encryption - Max File Encryption is a powerful yet easy-to-use encryption/steganography software. With Max File Encryption, you can encrypt files, hide files and create self-decrypting packages. The program uses the strong Blowfish algorithm, ensuring data safety Hermetic Stego - A steganography program which allows you to encrypt and hide a file of any size in BMP image files, with or without the use of a stego key, so that the presence of the hidden file is undetectable, even by software using statistical methods.
Hermetic Stego - A steganography program which allows you to encrypt and hide a file of any size in BMP image files, with or without the use of a stego key, so that the presence of the hidden file is undetectable, even by software using statistical methods. ViewPoint - To avoid any suspicion about your secret your file, it is hidden inside another file (your file is encrypted by the most modern and strong cryptographic algorithms) and the encoding program is also hidden inside another absolutely neutral program.
ViewPoint - To avoid any suspicion about your secret your file, it is hidden inside another file (your file is encrypted by the most modern and strong cryptographic algorithms) and the encoding program is also hidden inside another absolutely neutral program. MSU StegoVideo - Free program for hiding information in video. After info hiding you can compress video with unknown codec (this is main feature) and extract you file from this video later! Program advices lrelatively low noise level.
MSU StegoVideo - Free program for hiding information in video. After info hiding you can compress video with unknown codec (this is main feature) and extract you file from this video later! Program advices lrelatively low noise level. Puffer - Data file and e-mail encryption utility for Win 95 to XP. Uses 2048-bit Diffie-Hellman public key encryption with 256-bit AES algorithm for symmetric encryption.
Puffer - Data file and e-mail encryption utility for Win 95 to XP. Uses 2048-bit Diffie-Hellman public key encryption with 256-bit AES algorithm for symmetric encryption.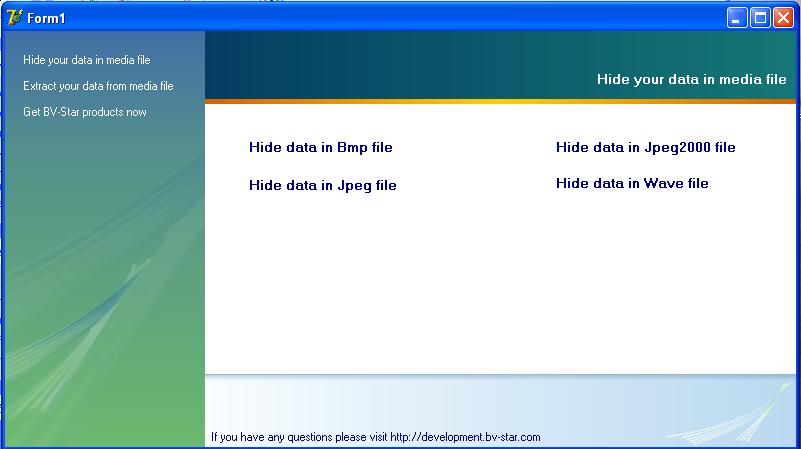 Steganography Lib - This Library gives you a unique opportunity to add steganography functions in your applications. With the help of this library you can give your applicaion ability to hide information in Jpeg, Jpeg2000, Wav, Bmp formats and so on.
Steganography Lib - This Library gives you a unique opportunity to add steganography functions in your applications. With the help of this library you can give your applicaion ability to hide information in Jpeg, Jpeg2000, Wav, Bmp formats and so on. Invisible Secrets Encryption Software - Keep those prying eyes out of your communications and prevent unwanted people from reading your private files. Invisible Secrets encrypts and hides data in places where not even your wife, boss, or a hacker would look for sensitive information.
Invisible Secrets Encryption Software - Keep those prying eyes out of your communications and prevent unwanted people from reading your private files. Invisible Secrets encrypts and hides data in places where not even your wife, boss, or a hacker would look for sensitive information. Xidie Security Suite - By combining cryptography with steganography, by using strong compression algorithms, well recognized and new encryption algorithms, classic and new steganographic techniques, Xidie Security Suite is one of the top steganography and encryption tools
Xidie Security Suite - By combining cryptography with steganography, by using strong compression algorithms, well recognized and new encryption algorithms, classic and new steganographic techniques, Xidie Security Suite is one of the top steganography and encryption tools CryptaPix - CryptaPix is an image file management and encryption program for Windows. Organize, print and secure your digital photos and downloaded image files. Resize, rotate, crop, and remove red-eye from photographs. Create standalone slideshows. Much more.
CryptaPix - CryptaPix is an image file management and encryption program for Windows. Organize, print and secure your digital photos and downloaded image files. Resize, rotate, crop, and remove red-eye from photographs. Create standalone slideshows. Much more.

 Top Downloads
Top Downloads
- Evidence Begone Free Porn Scan
- Agnitum Outpost Firewall Pro
- PasswordsPro
- SpotMSN Password Recover
- Zip Password
- Win Spy Software Pro
- KeysRecover
- Internet Access Controller
- Internet SPY - PC Detective
- Webroot Spy Sweeper with AntiVirus

 New Downloads
New Downloads
- DiskPulse Server
- SpyAgent
- Passwords Base
- Network Password Manager
- Cryper
- PasswordsPro
- SpotMSN Password Recover
- IE Asterisk Password Uncover
- Master Voyager
- ProteMac NetMine

New Reviews
- jZip Review
- License4J Review
- USB Secure Review
- iTestBot Review
- AbsoluteTelnet Telnet / SSH Client Review
- conaito VoIP SDK ActiveX Review
- conaito PPT2SWF SDK Review
- FastPictureViewer Review
- Ashkon MP3 Tag Editor Review
- Video Mobile Converter Review
Actual Software
| Link To Us
| Links
| Contact
Must Have
| TOP 100
| Authors
| Reviews
| RSS
| Submit